Do you want to know how to start a Career In Ethical Hacking? If yes, then this article is a perfect fit for your request. This article is based on research and market practices, which will lead you to the best options, among others.
One with interest in a career in ethical hacking can read this article to know how to start their search for the best source to learn ethical hacking skills. Ethical hacking is one of the best career options in the IT Sector, which will be beneficial for a bright future for IT professionals. Without wasting any time, let’s start talking about how to start a career in ethical hacking!
What is Ethical Hacking?
It’s the practice of lawfully exploiting the security flaws of a company’s system and networks to recognize its weaknesses and to access sensitive data without the consent of the authorities. In exchange for the data, adversaries can demand a ransom to release access to the captured resources.
Moreover, it involves using several cybersecurity tools and techniques to protect the resources against online threats that actively put the individual in a dangerous spot. Ultimately, with these skillsets, one can enhance the quality of their security measures to protect sensitive data against illegal possession. Let’s move further.
Role of an Ethical Hacker
An ethical hacker is responsible for carrying out the following tasks with the latest hacking techniques and tools.
- Vulnerability Assessment
To find potential vulnerabilities, ethical hackers test PC, Networks, and Apps. They scan and analyze systems using various tools & methods to look for vulnerabilities attackers might exploit.
- Penetration Testing
To imitate actual cyberattacks, professionals launch controlled & legal attacks on systems. While trying to exploit known flaws to obtain access without authorization, they steal sensitive data or interfere with system functions. It is to enhance security measures quality.
- Security Audits
To verify compliance with industry standards & best practices, professionals conduct deep audits of security policies, processes, and configurations. To find opportunities for enhancement, they examine network settings, access controls, encryption techniques, and other security measures.
- Security Research
Professionals keep up with the most recent security changes, flaws, & hacking methods. To improve their knowledge and abilities, they constantly explore fresh weaknesses and the latest threats.
- Reporting and Documentation
The vulnerabilities, techniques to exploit them, & possible effects of these loopholes are all things ethical hackers record in their research. They deliver deep reports explaining the consequences found & suggested solutions to system owners/ organizations.
- Security Consultancy
Firms frequently receive advice & recommendations from ethical hackers on how to improve their security posture. To reduce risks & improve overall security, they could advise putting security controls in place, providing security awareness training, or using a particular technology.
- Incident Response and Forensics
Professionals may help with incident response tasks in the event of a security issue/ breach. To help forensic investigations, they examine compromised systems, acquire proof, and offer insights into the nature of the attack.
What Is the Attraction of an Ethical Hacking Career?
Students are getting more n more attracted to the hacking line for the reasons mentioned below.
- Cybersecurity Demand
The demand for competent cybersecurity workers, especially ethical hackers, is growing due to the frequency and sophistication of cyber threats. Experts who can spot weaknesses, weigh risks, and defend against cyberattacks are needed by businesses of all sizes and in various sectors. Due to the great demand, there are several work opportunities and room for professional advancement.
- Challenging and Dynamic Work
Maintaining knowledge of the most recent hacking methodologies, security flaws, and defense strategies is necessary for ethical hacking, which entails continually changing problems. The field requires ongoing learning and skill improvement, which makes it enjoyable and intellectually stimulating. Since new technologies and attack vectors are continually being developed, the work is dynamic, keeping ethical hackers busy and presenting them with new difficulties.
- Contributing to Cybersecurity
A key component of protecting computer systems and networks is the use of ethical hackers. Ethical hackers actively assist in securing private data, preventing data breaches, and safeguarding vital infrastructure by spotting weaknesses and assisting companies in fortifying their defenses. For many people interested in a career in ethical hacking, the sense of mission and the chance to improve cybersecurity are major draws.
- Continuous Learning and Personal Growth
Deep knowledge of diverse technologies, network protocols, operating systems, programming languages, and security procedures is necessary for ethical hacking. Professionals need to stay up with the fast-changing dangers and defense tactics if they want to flourish in their area. This dedication to lifelong learning and personal development enables people to expand their knowledge and competence, which makes it a desirable quality of an ethical hacking job.
- Competitive Compensation and Job Stability
Firms are prepared to invest in cybersecurity personnel to secure their digital assets because there is a significant demand for ethical hackers. Because of this, professions in ethical hacking sometimes provide competitive pay and benefits as well as long-term employment. Competent, ethical hackers can command competitive pay packages and benefit from promising long-term career prospects if they have the necessary credentials and expertise.
- Ethical and Legal Framework
Unlike adversaries, ethical hackers act within the bounds of morality and the law. They are sanctioned and authorized to engage in hacking activities, ensuring their activity complies with moral principles and legal mandates. This distinction enables people to responsibly and constructively pursue their passion for hacking without facing legal repercussions.
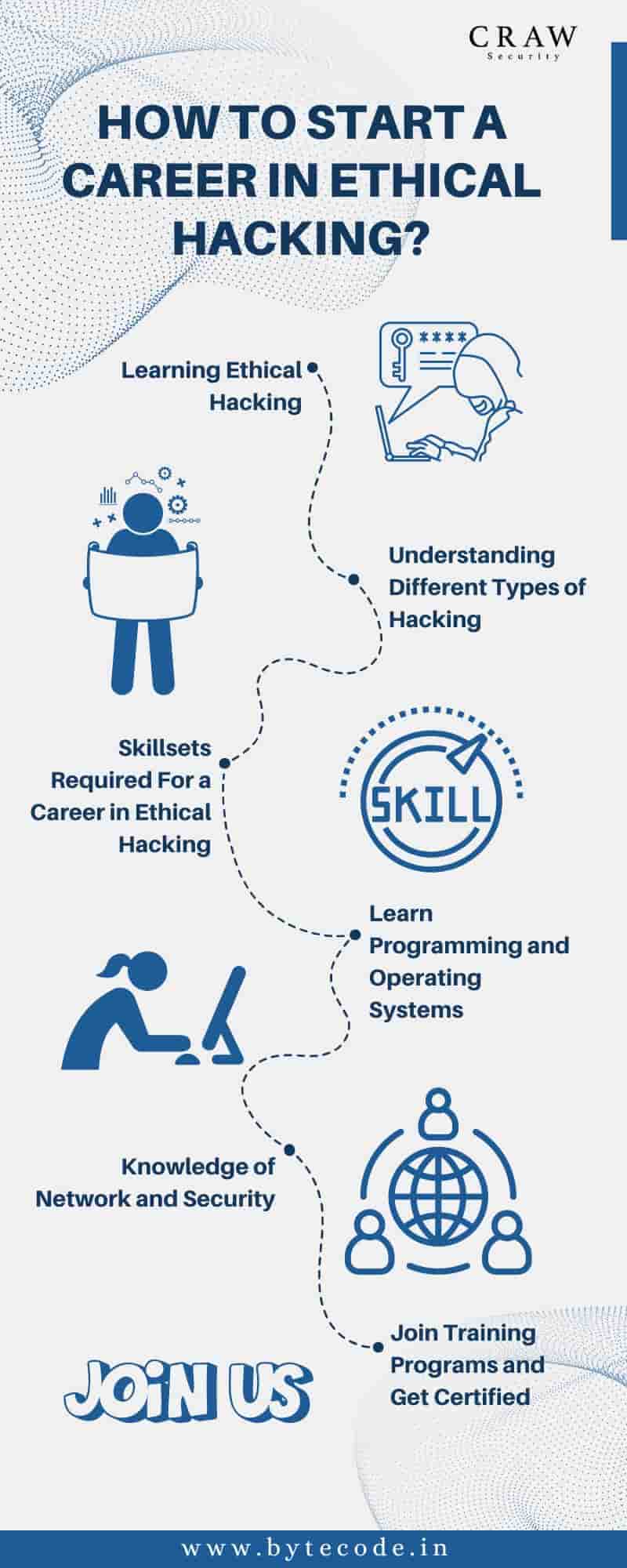
How To Start A Career In Ethical Hacking?
-Learning Ethical Hacking
-Understanding Different Types of Hacking
-Skillsets Required For a Career in Ethical Hacking
-Learn Programming and Operating Systems
-Knowledge of Network and Security
-Join Training Programs and Get Certified
If you want to start a career in ethical hacking, you can start with the following steps to pick up your pace in learning the mentioned skills and knowledge.
- Learning Ethical Hacking
First, educate yourself on the fundamentals related to ethical hacking. By taking advantage of the systems’ and networks’ current vulnerabilities, one can learn how ethical hacking strategy forms. Ethical hacking is a strategy for protecting system and network security to improve system and network security defenses. Moreover, ethical hackers use exactly the same methods as adversaries.
- Understanding Different Types of Hacking
Following are the mainstream 3 types of hackers:
- White Hat Hackers
- Black Hat Hackers
- Grey Hat Hackers
Grey Hat and White Hat hackers both engage in ethical hacking. Black hat hackers carry out malicious actions and criminal hacking somewhere for nefarious ends.
- Skillsets Required For a Career in Ethical Hacking
You’ll need to tolerate stress, think creatively, and have good problem-solving skills. To work in ethical hacking, you must also have a mindset emphasizing lifelong learning and development.
You must have great control over computing languages such as –
- HTML,
- ASP,
- C/C++,
- Python,
- Java, and
- Many more.
- Learn Programming and Operating Systems
One must have enough knowledge of programming languages due to the regular interaction with various systems. Moreover, you should be familiar with OS, including.
- Windows,
- UNIX,
- LINUX, and
- IOS.
Skills in programming languages are necessary for ethical hackers to detect errors or defects in code. In addition to other coding needs, installing security solutions that require coding and enabling task automation will make it easier.
- Knowledge of Network and Security
Professionals should be well-versed in computer networks and cybersecurity. An ethical hacker should have a firm understanding of both basic and advanced computer networking and data security concepts. These concepts include VPNs, cryptography, firewalls, and various cyberattacks, including DoS attacks.
- Join Training Programs and Get Certified
Due to the rising demand for ethical hacking skill sets, many training opportunities and courses have been available in the industry. Enroll in a boot camp or educational program to hone your skills and gain practical ethical hacking experience.
The worth and reliability of your professional profile as an ethical hacker are increased by earning certification. Thus, getting one is essential. With a signed certification from a reputable organization, such as Bytecode Security, you might land a position at a big tech business.
What Are the Stages of a Career in Ethical Hacking?
- Starting Out
Many students begin their studies by pursuing a computer science degree. Contact Bytecode Security if you’re looking for an Ethical Hacking Course in Delhi. This course will introduce you to various amazing ethical hacking concepts that will help you widen your horizons.
Moreover, your knowledge will start to grow eventually. After the sessions, you can take the ethical hacking examination, which will validate your skills for being a professional, ethical hacker.
- Network Support
Now that you have been certified, you can work practically in the field. You can start by being a networking professional. Your responsibilities will involve protecting networks by performing the following tasks.
- Tracking & Revisions,
- Setting up Security Software, and
- Checking for Vulnerabilities.
3. Network Engineer
You will now be designing and organizing networks rather than merely maintaining them. You should be concerned about security enhancements as you become an ethical hacker. Moreover, you can go for certifications such as
- Security+,
- CISSP, and
- TICSA.
Your duties will cover testing on essentials like
- Access Control,
- Identity Management,
- Cryptography,
- Risk Management,
- Cloud Computing, and
- App Development.
4. Working in Information Security
An information security analyst manages security gaps, examines network and system security, and works to develop security solutions. For this post, you should concentrate on penetration testing to gain practical experience with some of the required tools.
How to Become an Ethical Hacker With Zero Experience?
If you want to become an ethical hacker with zero experience, here are some steps you can follow:
- Gain a Strong Foundation in Computer Networks and Security,
- Learn Programming & Scripting,
- Understand OS,
- Study Web Tech,
- Practice yourself on dummy machines,
- Stay Updated,
- Obtain Certifications for ethical hacking,
- Join the Ethical Hacking Community, and
- Develop an Ethical Mindset.
What Tools Do Ethical Hackers Use?
Multiple tools are there that are employed by ethical hackers in order to catch vulnerabilities and perform several functionalities within a preferred work environment. In this regard, we have jotted down some mainstream ethical hacking tools that are commissioned by hacking professionals to do their multi-functionality works:
| Nmap | A strong open-source network scanning program utilized for security auditing and network investigation. It assists in building a network map by locating hosts and services on a computer network. |
| Wireshark | A network protocol analyzer that enables network packet capture and inspection. It aids in problem diagnosis and network traffic analysis. |
| Metasploit | A framework for penetration testing that makes it possible to identify, use, and confirm weaknesses in systems and applications. It aids in conducting thorough penetration tests. |
| Burp Suite | A platform with integrated security testing capabilities for web applications. It comes with a variety of tools for web vulnerability assessment, scanning, and exploitation. |
| Nessus | A well-liked vulnerability scanner that finds holes, configuration errors, and other security problems in networks and systems. |
| John the Ripper | A password-cracking program that uses a variety of methods to decrypt encrypted passwords and find weak passwords. |
| Aircrack-ng | A collection of tools for capturing and analyzing packets and trying to decipher WEP and WPA/WPA2-PSK keys in order to evaluate the integrity of wireless networks. |
| Nikto | A tool for scanning web servers for potential security flaws, configuration errors, and other problems. |
Difference Between an Ethical Hacker and a Penetration Tester
In evaluating and enhancing the safety parameters of computer systems, networks, and apps, ethical hackers and penetration testers have similar objectives. Nonetheless, there are some differences between the two job roles, such as the following:
| Ethical Hacker | Penetration Tester |
| An ethical hacker, also called a “white hat” hacker, is a cybersecurity expert who imitates criminal hackers’ tactics but does it with authorization and legal backing. | The role of an ethical hacker, known as a “pen tester” or penetration tester, is focused on evaluating the safety of a system via realistic attacks. |
| An ethical hacker’s primary goal is to find system flaws, vulnerabilities, and security gaps before malevolent hackers can take advantage of them. | Exploiting flaws and gaining illicit entry to a system, network, or application is the goal of penetration testing. Penetration testers conduct controlled and targeted attacks. |
| Similar to harmful hackers, ethical hackers undertake penetration testing and security assessments using a variety of tools and techniques. | Penetration testing’s main goals are to assess the efficacy of the company’s safety controls and to spot any potential vulnerabilities that require attention. |
| They abide by the law and a code of ethics, making sure that the system owners or other stakeholders have given their explicit consent before they engage in any activity. | Pen testers frequently adhere to set techniques, perform thorough evaluations, analyze the effects of successful assaults, and give the business in-depth reports. |
| Ethical hackers’ ultimate objective is to strengthen the target system’s security posture by offering suggestions and corrective measures. | Penetration testers operate within the bounds of the law and with the appropriate authorization from the corporation, much like ethical hackers. |
What Can You Expect as an Ethical Hacker?
You may anticipate a lively and gratifying career as an ethical hacker where you will actively find and fix security flaws in computer systems, networks, and applications. As an ethical hacker, you can anticipate the following major factors:
- Continuous Learning,
- Authorized Testing,
- Varied Work,
- Penetration Testing,
- Tool Familiarity,
- Reporting and Documentation,
- Collaboration,
- Problem-Solving,
- Ethical Responsibilities,
- Career Growth,
- Impactful Contribution, etc.
How to Gain Experience as an Ethical Hacker?
Learning, doing, and being exposed to real-world situations are all necessary to develop experience as an ethical hacker. The following actions can help you gain expertise in this area:
- Educational Foundation,
- Cybersecurity Certifications,
- Self-Study and Online Resources,
- Capture the Flag (CTF) Competitions,
- Ethical Hacking Labs,
- Open Source Projects,
- Bug Bounty Programs,
- Join Ethical Hacking Communities,
- Internships and Entry-Level Positions,
- Networking and Mentorship,
- Continuous Learning, etc.
Typical Ethical Hacking Assignments
White hat hackers, also referred to as ethical hackers, are given a number of tasks to evaluate the safety of computer systems, networks, and applications. Typical assignments for ethical hackers include:
- Threat Modeling
- Security Assessment
- Vulnerability Threat Assessment
- Report Writing
- Basic Hacking Skills
- Learn How to Program
- Learn to Use and Run an Open-Source Unix
- Learn How to Write HTML and Use the World Wide Web
Threat Modeling
In cybersecurity and software development, threat modeling is an organized method utilized to find possible hazards, weaknesses, and dangers to a system or application. This aids businesses in proactively evaluating security risks and choosing the best safety precautions to adopt.
Security Assessment
A business’s information systems, networks, and applications are subject to a systematic and thorough evaluation of security controls, risks, and vulnerabilities. A security assessment’s main goal is to pinpoint vulnerabilities and potential threats so that companies can take the necessary security measures and enhance their general safety precautions.
Vulnerability Threat Assessment
In order to detect potential holes and security problems, perform thorough vulnerability threat assessments of networks, servers, and applications.
Report Writing
Writing reports is a talent that is necessary for many industries, notably business, academia, and cybersecurity. Report writing is essential for sharing the outcomes of security audits, vulnerability discoveries, incident investigations, and other security-related tasks in the field of cybersecurity. A well-written report gives stakeholders brief, straightforward data that helps them comprehend safety concerns and make wise decisions.
Basic Hacking Skills
The fundamental information and skills needed by people who are interested in learning about computer systems, networks, and security flaws are referred to as basic hacking capabilities. It is crucial to make clear that hacking abilities can be applied both maliciously and unethically. Here, we concentrate on the ethical hacking scenario, when these abilities are employed ethically and legally to find and fix security flaws.
Learn How to Program
It’s a great talent to learn how to program because it offers up a wide range of career prospects in areas like software development, data analysis, artificial intelligence, cybersecurity, and more.
Learn to Use and Run an Open-Source Unix
It can be useful and inspiring to learn how to operate an open-source Unix-like operating system like Linux or BSD (Berkeley Software Distribution).
Learn How to Write HTML and Use the World Wide Web
The first step to building websites and utilizing the World Wide Web involves acquiring HTML (Hypertext Markup Language). The common markup language for structuring information on the internet is HTML.
Frequently Asked Questions
About How To Start A Career In Ethical Hacking
- Is ethical hacker a good career?
Definitely, ethical hacking can be the best option if you want to work in the IT Field as a security professional. Several students have already decided to become a part of the growing cyber security industry. Some of the reasons for which you should choose the ethical hacking as an option.
- High demand,
- Competitive salaries,
- Job security,
- Continuous learning & skill development,
- Contribution to cybersecurity,
- Variety of work environments, and
- Ethical & legal framework.
- Is ethical hacking a hard career?
Well, yes, it’s a competitive and challenging career option but, in return, also rewarding for the aspirants who really have a great interest in becoming top-gear administrative at high-end positions. Some of the complexity that you will see in a career in ethical hacking is as follows
- Technical complexity,
- Rapidly evolving landscape,
- Broad skill set,
- Problem-solving mindset,
- Continuous learning, and
- Ethical considerations.
- What is the salary of an ethical hacker?
An ethical hacker’s salary package can depend on various factors such as follows.
- Experience,
- Skills,
- Certifications,
- Employer, and
- Job Responsibilities.
- Entry-level or fresher positions – INR 3 to 6 lakhs/ annum,
- Mid-level ethical hackers – INR 7 to 15 lakhs/ annum,
- Senior-level ethical hackers – INR 15 lakhs/ annum.
- Are ethical hackers in high demand?
India has become a big hub for hacking aspirants for a few years. Moreover, movies based on the hacking life is also encouraging students to take part in such activities. For some, it has become a great inspiration, and for some, it took them to the wrong profession. Due to the high rate of cyberattacks, organizations need professional hackers to reduce such cases. Several factors contribute to the high demand for ethical hackers in India:
- Increasing cyber threats,
- Government initiatives,
- Compliance & regulations,
- Increasing awareness,
- Skill gap, and
- Growth of IT and e-commerce sectors.
- Does ethical hacking have a future?
Yes, the future of ethical hacking seems bright. The demand for knowledgeable people to safeguard computer systems and networks will increase as technology develops and cyber-attacks become more complex. Here are some of the explanations behind ethical hacking’s promising future:
- Increasing cyber threats,
- Evolving technology landscape,
- Regulatory requirements,
- Increased digitalization,
- Cybersecurity awareness, and
Career growth and opportunities.
6: How much money do ethical hackers make?
Based on a number of variables, notably their level of experience, competence, location, certifications, company, and the market need for cybersecurity professionals, ethical hackers’ salaries in India might vary widely. As of my most recent information update in September 2021, the salary range for ethical hackers in India is roughly as follows:
| Entry-Level Ethical Hacker | The annual wage range for those with little experience or who have just graduated from college is between INR 3 and 6 lakhs. |
| Mid-Level Ethical Hacker | Having some years of expertise and the necessary certificates, ethical hackers might make between INR 6 and 12 lakhs annually. |
| Senior Ethical Hacker | High-level experts with years of experience, advanced credentials, and a track record of success can earn salaries of INR 12 to 30 lakhs or more each year. |
| Consultants and Freelancers | In accordance with their professional standing and customer demand in the market, ethical hackers who work as independent consultants or freelancers may demand greater prices per project or on an hourly basis. |
7: Is ethical hacking in high demand?
Yes, the ethical hacking domain is very high in demand nowadays due to the sudden surge in the number of cyberattack incidents throughout the world on almost every third organization of any niche.
8: Which degree is best for hacking?
Several degrees are best for hacking in the current conditions of the market. Some of them are mentioned below:
- Computer Science/Computer Engineering,
- Information Security/Cybersecurity,
- Network Security/Network Administration,
- Software Engineering/Software Development,
- Mathematics and Statistics,
- Digital Forensics, etc.
9: What qualifications do I need to be a hacker?
You need a set of credentials, abilities, and traits to become a hacker, especially an ethical hacker or cybersecurity specialist. The use of hacking techniques ethically and legally to strengthen security and safeguard systems is known as ethical hacking.
Moreover, the main set of skills you need to require to become a fully functional ethical hacker is as follows:
- Formal Education,
- Technical Skills, such as
- Programming,
- Networking,
- Operating Systems information,
- Web Technologies,
- Certifications,
- Ethical Mindset,
- Problem-Solving Skills,
- Continuous Learning,
- Hands-On Experience,
- Communication Skills, etc.
10: Is ethical hacking future proof?
Yes, ethical hacking is generally considered to be future-proof due to several factors:
- Increasing Cyber Threats,
- Growth of Digital Transformation,
- Regulatory Compliance,
- Shortage of Cybersecurity Professionals,
- Emerging Technologies,
- Data Protection and Privacy Concerns,
- Bug Bounty Programs,
- Constant Evolution of Threat Landscape,
- Career Advancement Opportunities, etc.
11: Do you need a degree to be a hacker?
No, particularly when it comes to ethical hacking, you need not always require an official degree to be a hacker. The use of innovative problem-solving techniques to obtain unauthorized access to or influence computer systems or networks is referred to as hacking in its broadest definition. There are, however, primarily two categories of hackers:
- Malicious Hackers (Black Hat),
- Ethical Hackers (White Hat).
12: Is ethical hacking stressful?
Yes, ethical hacking may be stressful, particularly in particular circumstances and settings. The essential task of identifying and resolving security flaws in computer systems, networks, and applications is the job of ethical hackers, commonly referred to as penetration testers or cybersecurity experts.
13: Which age is best for ethical hacking?
Age is no bar who is willing to learn. However, there is no “best” time for ethical hacking in particular. People of all ages who are passionate about cybersecurity and have a keen interest in comprehending and safeguarding computer systems and networks are invited to pursue careers in ethical hacking. You may begin learning ethical hacking at any age, regardless of your age.
14: Does ethical hacking require coding?
Yes, coding abilities are often needed for ethical hacking. Coding is a key skill in ethical hacking since it allows attackers to automate numerous operations during penetration testing and security assessments by writing scripts and building bespoke tools.
15: What are the 5 types of ethical hacking?
The 5 types of ethical hacking techniques are as follows:
- White Box Testing,
- Black Box Testing,
- Gray Box Testing,
- Internal Testing,
- External Testing, etc.
Wrapping Up
In the bottom line, we would like to say that we have implemented to elaborate every minor to major detail related to a great Career In Ethical Hacking. In this context, you can start a very mesmerizing 1 Year Cyber Security Diploma Course by Bytecode Security, the best cybersecurity training institute in Delhi NCR, to deliver world-class cybersecurity education under the prominent guidance of an international educator. To know more about the same, give us a call at our 24-hour hotline mobile number, +91-9513805401, and have a word with our highly experienced educational counselors.