Wireless Penetration Testing Service in India
Companies nowadays have advanced their technologies to keep up with the ever-developing industry trend. Also, to offer security, organizations maintain their websites and apps perfectly coordinated with the networks and server implants.
As you can see, if the network connects the company’s several departments, you must know that the data of all departments is interconnected. These networks hold the data in packet format that could be quickly snatched or snuffed during data transfer.
Whether you’re running a small-scale or large-scale industry company, you need to protect your data related to customers, business, finance, and the owner’s confidential data. Wireless Penetration Testing can ensure that your network is safe enough to hold the responsibility of millions.
Let’s continue with how you can protect your networks from getting hacked by unauthorized users or hackers. To do that, you can rely on a Wireless Penetration Testing service. The networks will be examined using a method similar to the standard wired penetration test.
However, to get the perfect overview, they will focus on wireless as the gateway to exploit the vulnerabilities. You need experts to deal with your network and do Wireless Penetration Testing.

What is security penetration?
Security penetration means the practitioner will execute several attempts on your devices to check whether they are compatible enough to prevent malware attacks or unauthorized access. These attempts are professionally made by a hacker with the skills and knowledge to trespass into your network or system to exploit the vulnerabilities within minutes.
There can be several incidents where you do not hire the hacker. Sometimes it could be the adversary wants to steal confidential data to threaten you with getting ransom money in exchange for a decryption key or the data they steal from you.
Now you might be wondering: what is Wireless Penetration Testing? How does the Wireless Penetration Testing methodology help you out? Wi-Fi Pentest is needed to know the issues left in the network. Sometimes, the Wireless Penetration Testing checklist can help prevent unauthorized access to your network or system.
In simple terms, Wireless Penetration Testing will help you identify vulnerabilities in the network that could be exploited by hackers online. You will be able to save your network and connected devices from adversaries who are experts in hacking skills. Now, let’s see what steps must be taken while performing a Wireless Penetration Test.
Crawsecurity.com is one of the best service providers for Wireless Penetration Testing Services. If you want to professionally handle the issues related to your networks and servers, you can contact us without hesitation.
Steps To Performing a Wireless Penetration Test
Step 1: Wireless Reconnaissance
Before any Wi-Fi attack, you must gather information about the nature of Wi-Fi. Just because of the nature of wifi, the data you collect will be possible via War Driving. It’s a kind of data-gathering method that involves walking around a platform to sniff Wi-Fi Signals.
To do that, you need tools like:
- A vehicle
- Lappy and A Wifi Antenna
- Wireless Network Adapter
- Packet Capture and Software Analysis.
Unfortunately, most of the time, the data you could be able to gather will be helpful. Sometimes the data might be encrypted because if the company uses the latest Wi-Fi Protocol (WPA2), it might not be easy to get the data. Wi-Fi Protocols are available to protect access points via encryption and EAPOL Authentication.
Step 2: Identify Wireless Networks
After you get enough data about the nature and workings of Wi-Fi, you can scan/ identify the wireless network.
Before the scan, you must put your wireless card in “monitor” mode. That’s to enable packet capturing and specify your WLAN interface.
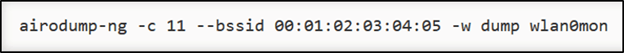
When your wireless card starts working and listening to wireless traffic, you can start the process of scanning with Airodump to scan traffic on various channels.
It’s an important step to be taken to reduce workload during the scanning process of scanning. That’s to force the airodump to collect traffic on the targeted channel.
Step 3: Vulnerability Research
Next, after you scan the wifi access points, the next step is to identify the loopholes in the access point. The most common loophole you’ll discover is in the 4-way handshake process. The encrypted key will be exchanged through the Wi-Fi Access Point and the Authenticating User.
A pre-shared key is generated and transmitted in the Wi-Fi Access Point Authentication process. During the critical transmission, an adversary can sniff the key and use brute force on it offline to extract the password. In the next step, we’ll learn about the pre-shared critical sniffing attack and the tools used to complete the assessment.
For Vulnerability Research, you can get support from bytecode.in because we have provided assistance to several organizations with vulnerability searches in their networks and servers.
Step 4: Exploitation
Now that you’ve got the vulnerability, it’s time to exploit it. To do that, we will use the Airplay NG suite tool to complete exploitation. The use will involve:
- De-authenticating a Legitimate Client
- Capturing the initial 4-way handshake at the time the client tries to reconnect.
- To crack the captured key, run an offline dictionary attack.
If an adversary succeeds in this step, he’ll be able to access all traffic passing via that access point.
Step 5: Reporting
After you have tested the network, preparing the results of steps, methods, and findings into a document is necessary. In the report, you must mention every step you took to ensure the completion of the task. Not a single point must be left out of the report. Detailed technical risks, observed vulnerabilities, exploitation methods, and mitigation recommendations must not be left behind.
Step 6: Remediation and Security Controls
After any attack mentioned, remediation and Security Controls are necessary. The attack is a method to find the vulnerability and tell the users that you have found the loopholes that need a security patch. Also, if you have some techniques to tell them, make sure that the techniques don’t cause any harm to the security measures or policy of the company.
Understanding Wireless Penetration Testing for Business
Wireless Penetration Testing is beneficial and essential for every company you might see in the industry. The reason is that every business, such as yours, is connected to the internet and needs the help of Wireless Penetration Testing to find out the loopholes in your network management.
After that, you can quickly go for more secure ways for your networks and systems. That will change your attitude towards your business management and your thoughts on considering your data’s safety online.
A WiFi Assessment is necessary to strengthen your security around the world. Several hackers want to snatch data from open networks with loopholes.
Benefits of Wireless Penetration Testing
- With the help of this, you can find out the vulnerabilities in your network.
- You can learn how many loopholes your network has to patch.
- The techniques will help prevent unauthorized access.
- Prevent data breaches via network hijacking.
Frequently Asked Questions
About Wireless Penetration Testing Service in India
What are the 5 stages of penetration testing?
The 5 stages of penetration testing are as follows:
● Reconnaissance
● Scanning
● Vulnerability Assessment
● Exploitation
● Reporting
The steps will be taken professionally by experts and the stages will clear where are the loopholes in the system and where should you make a patch ready for it.
What are pen testing tools?
Several popular pen testing tools are used in penetration testing to find vulnerabilities faster. Some of them are as follows:
● Powershell-Suite
● Zmap
● Xray
● SimplyEmail
● Wireshark
● Hashcat
● John the Ripper
● Hydra
What is the WIFI pineapple?
It’s a wireless auditing platform via Hak5. This platform allows network security admins to execute penetration testing. Penetration testing is a kind of ethical hacking that is run on devices to find vulnerabilities that could be exploited by adversaries.
What is wireless penetration?
Wireless Penetration is a kind of pentesting that helps to find the loopholes in the security of a network and with the help of this testing, practitioners can find solutions to prevent any illegal access to happen on networks and also prevent data breaches.
What is firewall penetration?
A firewall is one of the best security measures that stop hackers from trespassing into any website and exploiting vulnerabilities to get the data out of databases. With the help of firewall penetration, you will be able to know how many loopholes are in your firewall that you have prepared for your websites. After that, you can prepare better security measures.