Certified Ethical Hacker CEH v13 AI Training Course | Bytecode Cyber Security
With the increase in cybercrime, it has become important to know how and why the attackers attack a system, and more importantly, how can these attacks be counteracted and prevented. The major attacks are done on the sensitive information of an organization, as it is one of the most valued assets in companies.
Information security is the protection of data, irrespective of its form, as valuable and meaningful data can be stored in many forms, while cyber security deals with the protection of data that is being generated in digital form only in systems and networks.
Hacking refers to the legal or illegal gain of access to a system or network by experts, while ethical hacking refers to the hacking of a system or a network by the expert but not with malicious intent.
Elements of Information Security
- Confidentiality: This means that only authorized people can access the information.
- Integrity: is the assurance that the information has been passed from the sender to the destination as it was supposed to be. No tampering has been done with the data.
- Availability: It refers to the availability of devices used to exchange information with users when required.
- Authenticity: Assurance that the quality of data is authentic and uncorrupted.
- Non-Repudiation: It is a way to guarantee that the sender has sent the data while the receiver has received it. Either of both cannot be denied later.
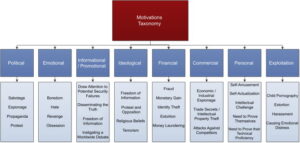
Motives of Attack
Classification of Attacks
- Active Attack- These are the direct attacks performed on the systems in which the attackers launch detectable traffic into the network to exploit the information.
Examples- DOS attack, MITM, SQL injection, backdoor access, spoofing attacks, etc.
- Passive Attack- In this attack, contrary to an active attack, the attacker uses sniffers to capture the data without the consent of the user, which is being transmitted from one end to another.
Examples- Footprinting, sniffing and eavesdropping, network traffic analysis, and decryption of weakly encrypted traffic.
- Close-in Attack- These attacks happen when the attacker is in close proximity to the network or the target system. The main goal is to gather, modify, or disrupt the information.
Examples- Social engineering
- Insider Attack- It is performed by a trusted person who has access to sensitive information about the organization.
Examples- Eves dropping and wiretapping, social engineering, data theft, spoliation, etc.
- Distribution Attack- These attacks are performed even prior to the installation of the hardware or software. Attackers in this attack, tamper the source code before the installation.
Examples- Modification of hardware or software during production or distribution.
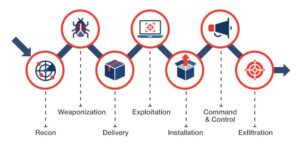
Cyber Kill Chain Methodology
- Reconnaissance- It means gathering information about the target system or network to identify a loophole before attacking.
- Weaponization- In this step, the attacker analyses the data gathered in order to select an appropriate tool to attack the system or target network.
- Delivery- It is the stage in which the attacker attacks its target. It could be through any form as decided by the adversary in the previous step. This is the stage in which the effectiveness of defense strategies of a system becomes known.
- Exploitation- Once the delivery is done, the malicious code of the attacker starts to trigger exploitation in the target system. It is where the organizations face authenticity and authorization attacks.
- Command and Control- In this stage, the adversary creates a path for 2-way communication from the server controlled by him to the victim’s system to pass data back and forth continually.
- Actions on Objectives- The attacker finally gets what he seeks. He gets either the confidential data he was looking for, or the target network or service are being disrupted, or the operational capability of the target has been compromised.
Indicators of Compromise
The system we use in our daily lives tends to behave oddly when it’s attacked. The indications of the system that point towards an intrusion are the indicators of compromise. A continuous check on the system and network should be performed by security professionals to detect any threat to the system and counteract it. They need to remain updated an keep updating their system and network to detect and respond to evolving cyber threats. IOCs are not intelligence but do serve as a source of information for an organization to enhance their strategies to prevent and handle any attack.
Categories-
- Email Indicators- Malicious data is sent through Email.
- Network Indicators- These are useful for command and control, malware delivery, identifying operating systems, and other tasks.
- Host-Based Indicators- Indicators given by the infected system within the network of an organization.
- Behavioral Indicators- These are used to identify behavior related to a specific attack.
Hacking
Hacking refers to the exploitation of system and network vulnerabilities to gain access to the system. It involves the compromise of security systems and confidential data, or modifying system or application features that are unwanted by the authorized user.
A hacker is an intelligent and skilled individual who can create and explore hardware and software and discover vulnerabilities in the target system.
Classes of Hackers
Apart from these, there are-
- Green Hat Hackers- A hacker who is a newbie in the hacking game but is working hard to excel in it.
- Red Hat Hackers- Hackers who target Linux systems.
- Purple Hat Hackers- Hackers who test themselves on their PC.
- Blue Hat Hackers- Security professionals who are outside the organizations. They come to check the vulnerabilities of systems and the network.
- Elite Hackers- These are pro-hackers and takes years of practice to be one.
Phases of Hacking
- Reconnaissance- In this, the attacker gains information about the target system or network before launching an attack. It is done to know the loopholes and back door to entry and exit into one.
Types–
- Active Reconnaissance- Direct interaction is done with the target.
- Passive Reconnaissance- Direct interaction is not done with the target.
- Scanning-
- Pre-Attack Phase- The attacker uses the gathered information to scan the network for specific information.
- Port Scanner- Scanning by using dialers, port scanners, network mappers, ping tools, and vulnerability scanners.
- Extract Information- Information is extracted to launch attacks.
- Gaining Access- This phase in which the attacker gains access to the OS or applications on the target system.
- Maintaining Access- In this phase the attacker tries to own the system by snatching the authorship of the authentic user over the system and also preventing other attackers from entering into it.
- Clearing Tracks- It is done by the adversary to clean their tracks in order to hide their identity. The attacker overwrites the server, system, and application logs to avoid suspicion.
Information Security Laws and Standards
Payment Card Industry Data Security Standard (PCI DSS)- It is an information security standard that takes care of credit cards.
ISO/IEC 27001:2013- It specifies the requirements for establishing, implementing, maintaining, and continually improvising an information management security system within an organization.
Health Insurance Portability and Accountability Act (HIPPA)- It deals with healthcare transactions, code sets, and identifiers.
Sarbanes Oxley Act (SOX)- These are financial standards to protect both, investors and the public by increasing the accuracy and reliability of corporate disclosure.
DMCA and FISMA- These standards deal with plagiarism and copyright information.
Frequently Asked Questions
About Ethical Hacking Training Course in India
Q. 1: What are the prerequisites for doing CEH certification?
The prerequisites for doing CEH Certification are as follows:
● A least 2 years of experience in the IT Security domain.
● A basic understanding of networking and security concepts.
● A valid CEH credential from a trusted certification body.
● A minimum of 21 hours of instructor-led training.
● Successful completion of the CEH exam.
Q. 2: What is the CEH (Certified Ethical Hacker) course?
The Certified Ethical Hacker (CEH) is a course offered by the International Council of Electronic Commerce Consultants (EC-Council). It is designed to provide information security professionals with the necessary skills and knowledge to protect organizations from malicious attacks.
Moreover, the course covers the five phases of ethical hacking: reconnaissance, gaining access, enumeration, maintaining access, and covering tracks. It provides students with the ability to conduct security assessments and penetrate networks in order to identify potential threats and vulnerabilities.
In addition to this, the course also covers topics such as intrusion detection, social engineering, denial-of-service attacks, and more. Upon completion of the course, students will receive an industry-recognized CEH certification.
Q. 3: How much does CEH v13 AI cost in India?
The cost of CEH v13 AI in India is around ₹40,000/-. However, it can come to a certain lower price to the candidates hailing from a financially weaker or socially disadvantaged section by doing it from Bytecode Security, a subsidiary of Craw Security, an accredited partner of EC-Council to deliver their information security courses at very competitive prices.
Q. 4: How long is CEH v13?
The Certified Ethical Hacker (CEH) v13 AI certification program is a comprehensive course consisting of 20 modules that take time to complete. However, at Bytecode Security, one may do this explicit knowledge-possessing course in a mere 40 hours of training part.
Q. 5: How much does CEH certification cost?
The cost of Certified Ethical Hacker (CEH) certification depends on the provider. Generally, the international cost ranges from $750 to $2,000. Moreover, this prominent EC-Council CEH v13 AI certification is something around ₹40,000/- in India.
Q. 6: Is CEH v12 for beginners?
Yes, the Certified Ethical Hacker (C|EH v13) certification is suitable for beginners.
Q. 7: What does a C|EH do?
A Certified Ethical Hacker (C|EH) is a professional who understands and knows how to look for weaknesses and vulnerabilities in target systems and uses the same knowledge and tools as a malicious hacker, but in a lawful and legitimate manner to assess the security posture of a target system. They use their skills to perform penetration testing, verify security controls, perform security assessments, identify vulnerabilities, and develop mitigation strategies.
Q. 8: Is C|EH worth pursuing?
The Certified Ethical Hacker (C|EH) credential is an industry-recognized certification that validates a person’s ability to identify, analyze, and mitigate security threats within an organization. Hence, it is an excellent credential to pursue if you are interested in a career in information security.
Q. 9: Is C|EH a good certification?
Yes, the Certified Ethical Hacker (C|EH) certification is a good certification to have. It is a globally recognized certification that demonstrates a professional’s knowledge and skills in ethical hacking and information security. In addition, it is highly valued by employers and can help open career opportunities in the field of information security.
Q. 10: How much money does a certified ethical hacker make?
The average salary of a Certified Ethical Hacker ranges from $45,000 to $120,000 per year, depending on experience and the specific role.
Q. 11: Is C|EH a popular cybersecurity certification?
Yes, the Certified Ethical Hacker (C|EH) certification is a popular cybersecurity certification. In addition, it is one of the most sought-after certifications in the field and is designed to help individuals develop their ethical hacking skills.
Q. 12: Is C|EH in demand?
Yes, C|EH is in demand in the cybersecurity field. According to the Global Knowledge 2020 IT Skills and Salary Report, Certified Ethical Hacker (C|EH) ranked second on the list of the top-paying certifications, with the average salary of certified professionals reaching $125,933.
Moreover, the survey also found that the demand for certified ethical hackers has been consistently growing year over year.
Q. 13: Why Should I consider getting the C|EH?
The Certified Ethical Hacker (C|EH) is an industry-leading certification that is designed to demonstrate the holder’s proficiency in ethical hacking and penetration testing. In addition, it offers an in-depth understanding of network security threats, vulnerabilities, and the tools used to counter them.
By obtaining the C|EH, you will gain a comprehensive understanding of hacking techniques, how to identify threats, and how to defend against them. Additionally, the certification increases your marketability to potential employers and can also open up opportunities for career advancement.
Q. 14: After I get certified, does EC-Council help with job placement?
No, the EC-Council does not directly help with job placement, but it does offer resources to help with job placement such as its job board and career resources.