Online AWS Security Summer Internship in Delhi 2025
The Security Engineering on AWS Security Summer Internship training course helps you build extensive knowledge to keep yourself secure in AWS Cloud using AWS security services. The training encompasses the recommended security practices by AWS Security along with security practices, security features of AWS key services including compute, storage, networking, and database services. Learnings concerning AWS services and tools for automation, continuous monitoring with logging, and responding to security incidents.
Students can attend classes from their homes. It takes less time to attend an online class. At the same time, various groups can attend online classes with bytecode Cyber Security From home.
AWS Security Summer Internship Course Module
MODULE 01: Given an AWS Abuse Notice, Evaluate a Suspected Compromised Instance or Exposed Access Key
MODULE 02: Evaluate the Configuration of Automated Alerting and Execute Possible Remediation of Security-Related Incidents and Emerging Issues
MODULE 03: Verify that the Incident Response plan includes relevant AWS services
MODULE 04: Design and implement security monitoring and alerting
MODULE 05: Troubleshoot security monitoring and alerting
MODULE 06: Design and Implement a Logging Solution
MODULE 07: Troubleshoot Logging Solutions
MODULE 08: Design Edge Security on AWS
MODULE 09: Design and implement a secure network infrastructure
MODULE 10: Design and Implement a Scalable Authorization and Authentication System to Access AWS Resources
MODULE 11: Troubleshoot a secure network infrastructure
MODULE 12: Design and implement host-based security
MODULE 13: Troubleshoot an Authorization and Authentication System to Access AWS Resources
MODULE 14: Design and implement a data encryption solution for data at rest and data in transit
MODULE 15: Troubleshoot key management
MODULE 16: Design and implement key management and use
Who this AWS Security Summer Internship Training Course is for :
- Security engineers Interested in Deploying Applications on AWS Security.
- Any IT professional who wants to learn AWS Security.
- Employees can pursue this security course.
- Beginners who want to understand AWS Security course.
- Security architects.
What is New in AWS Security Summer Internship Course?
- AWS shared security responsibility model.
- Encryption techniques.
- Applying security checks to conduct an automated and reproducible infrastructure.
- Troubleshoot key management.
- Design and implement host-based security.
Our Students Placed in Companies




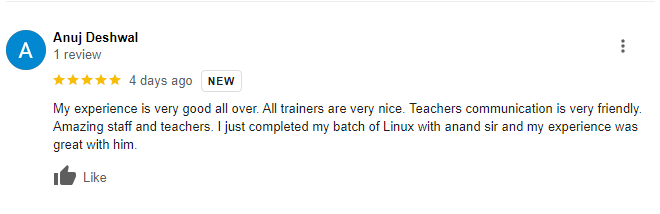
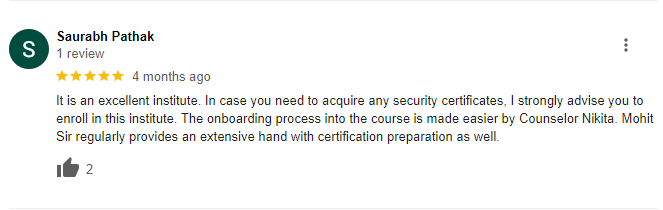
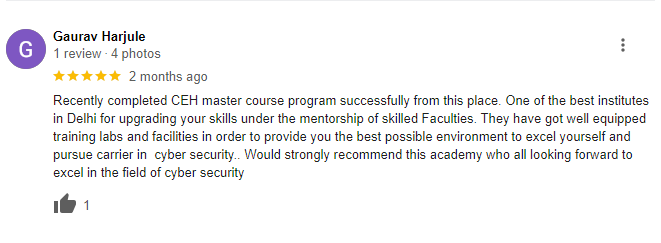
Our Google Reviews
Frequently Asked Questions
About The AWS Security Training Course Program
What does AWS use for security?
Many different security protocols are used by Amazon Web Services (AWS) to safeguard its cloud computing services. Virtual private clouds (VPCs), firewalls, identity and access management (IAM) regulations, and data encryption are some examples of these technologies. Other security services offered by Amazon Web Services (AWS) include AWS Inspector, which conducts security checks, and AWS Shield, which defends against DDoS attacks.
How many types of security are there in AWS?
The security features of Amazon Web Services (AWS) are divided into six categories. These topics include Network Safety, Application Security, Data Encryption and Protection, Identity and Access Management (IAM), Logging and Monitoring, and Infrastructure Security.
Does AWS have good security?
Data protection, identity and access management (IAM), multi-factor authentication (MFA), and encryption are just a few of the many security features that AWS provides. Furthermore, Amazon Web Services (AWS) offers a range of solutions to assist clients in safeguarding their data and applications against dangers like hostile entities and Distributed Denial of Service (DDoS) attacks.
Does AWS have firewall?
AWS Network Firewall is a managed service that makes it easy to deploy essential network protections for all of your Amazon Virtual Private Clouds (VPCs). AWS Network Firewall includes features that provide protection from common network threats.
What are the key benefits of AWS Security?
A person may consider enrolling in a reputable institution like Craw Cyber Security Institution, which has branches in Saket and Laxmi Nagar, after working for five to ten years as an AWS Associate in a cloud-based company. This company offers a comprehensive AWS Security Course, instructed by highly skilled and experienced professionals in the field.
How hard is AWS Security exam?
Exam-taking procedures don't provide a very high level of complexity. In my assessment, the level of complexity on this exam is slightly greater than associate-level exams, but significantly lower than professional-level exams. Furthermore, if you dedicate yourself entirely to it for a duration of around two months, you will gain a current and comprehensive understanding that will equip you for any pertinent work in the AWS Security domain.
Which is the hardest AWS Security certification?
In terms of difficulty, the three most challenging Associate-level AWS Certifications are the Developer, AWS Solution Architect, and SysOps Administrator certifications.
Furthermore, when referring to professionals, the title is known as the Solution Architect Professional.
Do AWS certifications expire?
AWS Certifications are valid for three years. To maintain your AWS Certified status, we require you to periodically demonstrate your continued expertise through a process called recertification.
What is the difference between an exam and a certification?
An exam is a test that validates an individual’s technical knowledge of AWS products and services. A certification is a credential that you earn upon successfully passing an exam. This credential is a digital badge and title that you may use on your business cards and other professional collateral to designate yourself as AWS Certified
How do I prepare for AWS security specialty ?
To pursue the AWS Certified Security - Speciality certification, you must first get the AWS Associate Certification. After that, it is expected that the candidate has a significant professional background spanning five to ten years as an accredited AWS Associate Professional working for a reputable IT company.
What are biggest AWS security vulnerabilities?
It has been demonstrated that the Amazon Web Services (AWS) infrastructure has several significant security vulnerabilities. These vulnerabilities are listed as follows:
- Unsecured Cloud Storage
- Unpatched Systems and Software
- Misconfigured Security Groups
- Insecure APIs
- Weak Identity and Access Management
- Exposed Credentials
- Unencrypted Data
What are the risks of AWS?
The following are the main risks connected to Amazon Web Services (AWS):
- Security Risks: While Amazon Web Services (AWS) offers a dependable and secure platform, it is important to keep in mind that customers are ultimately responsible for ensuring the security of their own systems and data. Users using AWS are entirely responsible for safeguarding their apps and data, as well as for ensuring that their configurations adhere to recognized security best practices.
- Data Loss Risks: Data protection and backup are the responsibility of AWS customers, who also need to take the appropriate safety measures to safeguard their data. Users must take security procedures to guard against potential data loss because AWS cannot guarantee the security of client data.
- Cost Risks: Customers of Amazon Web Services (AWS) are responsible for managing their own cloud expenses and can incur additional fees if their usage goes over what they had anticipated.
- Compliance Risks: It is the responsibility of AWS customers to make sure that their apps and data comply with all relevant laws and regulations. Amazon Web Services (AWS) provides customers with a variety of resources and assistance to help them fulfill their legal requirements. However, to ensure that they are following compliance standards, customers must take the appropriate actions.
Does AWS provide a firewall?
The Intrusion Prevention System (IPS), also referred to as the AWS Network Firewall, provides dynamic network flow inspection to detect and prevent the exploitation of vulnerabilities through signature-based detection.
Furthermore, AWS Network Firewall has web filtering capabilities that effectively restrict traffic to known dangerous URLs and enable fine-grained management over fully qualified domain names.